The procedure to add a trusted device to an IP address whitelist is as follows:
- Navigate to Quick Menu > System > Configuration > Integration Management. The Integration Management window is displayed.
- Expand the supported multi-factor authentication entry from within the nested 2FA Integration classification structure and select an associated integration service from the alphabetical list (or enter its name into the Search Integrations field). By default the list is filtered to show Current integration services. An alternative filter can be applied using the Select view drop-down field: Expired, Future or All combinations
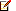 1.
1.
- Click on Whitelist Configuration. The Whitelist Configuration tab is activated.
- Click on Add Whitelist IP. The Add Whitelist IP window is displayed.
- To specify a single or group of known IP addresses: (1) Using the Rule type drop-down field, select the specific parameter value of Absolute IP; (2) Enter the IP address syntax for one or more trusted devices into the Absolute full IPs field provided
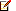 2; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
2; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
- Alternatively, to specify the upper and lower IP address thresholds for the range of devices in circulation: (1) Using the Rule type drop-down field, select the specific parameter value of IP Range; (2) Enter the lowest and highest IP address values into the corresponding From and To fields provided; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
- Otherwise, to identify the IP address structure elements that are known to vary within the expected network and host permutations: (1) Using the Rule type drop-down field, select the specific parameter value of Wildcard; (2) Enter the accepted IP address pattern into the Wildcard field provided
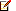 3; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
3; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
- Click on Save. The new trusted device entry is displayed in the Whitelist IP Rule Details summary table.
 Note
Note
1 The Search Integrations field will match against any element of the multi-factor authentication vendor.
2 A comma separator allows multiple IP addresses to be included within the same whitelist entry.
3 An asterisk (*) character is employed in any octet known to vary within the expected network and host permutations.
See related topics...
Two factor authentication management overview
 1.
1. 2; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
2; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid. 3; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid.
3; (3) Choose an Effective from date for this IP address whitelist entry i.e. the date on which it came into effect; (4) Choose an Effective to date if the whitelist entry is to be reviewed on a specific date or to capture a change of circumstances - a blank field means the security compliance status for these trusted devices will be continually valid. Note
Note